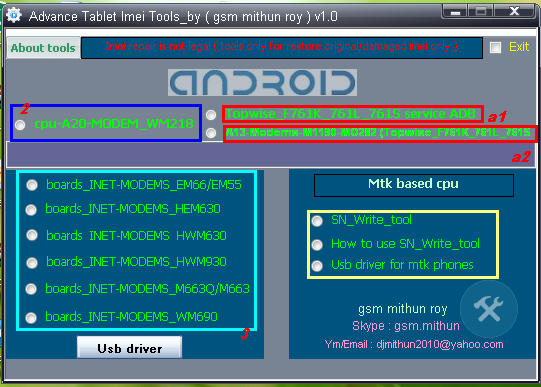
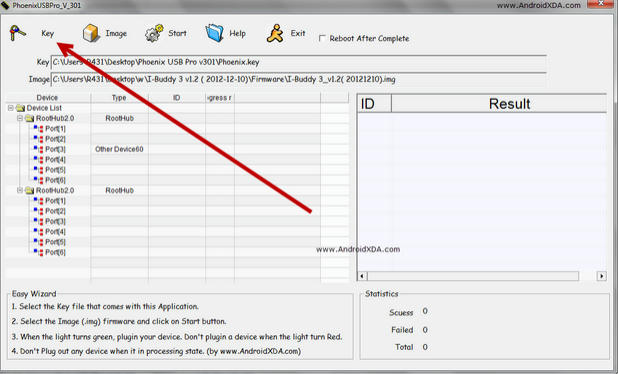
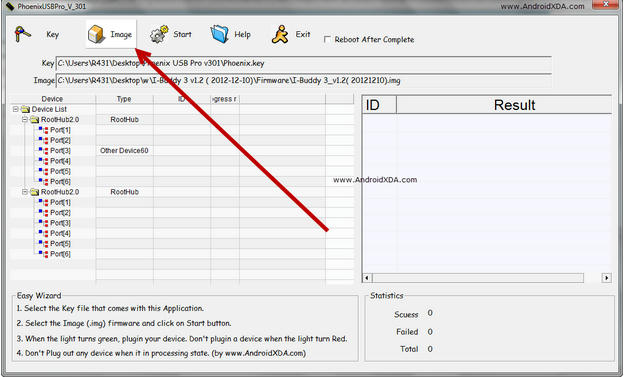
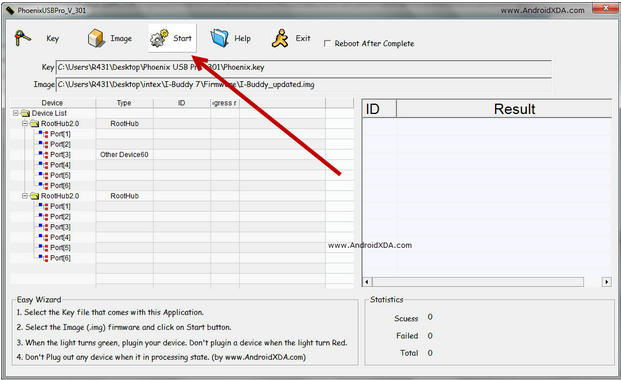
Agustus 2015 - First announced in March 2017, the Xperia L1 has come to replace Sony’s now discontinued E series. Priced at a surprisingly cheap £169, the L1 is Sony’s newest attempt at shaking up the budget phone market. Its large screen and sleek design make us think of Sony’s higher range of smartphones: it would be hard to single it out as the cheapest model in a line of Xperias. But at such a bargain price, we can’t expect it to perform as well as its more expensive counterparts. So how does the L1 hold up to other low-budget smartphones? Here’s our Xperia L1 review.
first time the View branding, well we have collected a lot of data from the field directly and from many other blogs so very complete his discussion here about Agustus 2015, on this blog we also have to provide the latest automotive information from all the brands associated with the automobile. ok please continue reading:
(Updated: September 7, 2015)
On August 15,
The New York Times and
Pro Publica published a story in which the big US telecommunications company
AT&T was identified as a key partner of the NSA.
Interesting details about this cooperation and the cable tapping were already in the 2008 book
The Shadow Factory by James Bamford, but with the new story, also a number of clarifying documents from the Snowden-trove were disclosed.
Among them are some powerpoint presentations that contain the slides which had been shown on Brazilian televion two years ago. They were first
http://firsttimetheviewbranding.blogspot.com /2014/01/slides-about-nsas-upstream-collection.html">discussed on this weblog in January 2014.
Here we will combine these new and old documents to provide a detailed picture of this important collection program, that was previously misunderstood on various occasions.
 The AT&T switching center at 611 Folsom Street, San Francisco,
The AT&T switching center at 611 Folsom Street, San Francisco,
where there's a cable access under the FAIRVIEW program
(Photo via Wikimapia - Click to enlarge)At NSA, the division Special Source Operations (SSO) is responsible for collecting data from backbone telephone and internet cables. For that, SSO also cooperates with private telecommunication providers under the following four programs, which are collectively referred to as
Upstream Collection:
- BLARNEY (collection under FISA authority, since 1978)
- FAIRVIEW (cooperation with AT&T, since 1985)
- STORMBREW (cooperation with Verizon, since 2001)
- OAKSTAR (cooperation with 7 other telecoms, since 2004)*
Before the new revelations, it was often assumed that BLARNEY was the program for NSA's cooperation with AT&T. The
Wall Street Journal reported this in August 2013, based upon former officials, saying that BLARNEY was established for capturing foreign communications at or near over a dozen key international fiber-optic cable landing points. This assumption was also followed by Glenn Greenwald in his book No Place to Hide from May 2014.
In a
letter to Cryptome, James Atkinson suggests that BLARNEY was the covername for cooperation with AT&T since 1978, and that after the
Bell break-up, BLARNEY stayed active for FISA collection, and the new covername FAIRVIEW was created for the "new" AT&T. One new
slide however, shows that BLARNEY actually encompasses all (over 30) companies that are cooperating for FISA collection, including of course AT&T and Verizon.
SpeculationsThe assumption that BLARNEY was the program for AT&T left room for speculation about the purpose and scope of the FAIRVIEW program.
For example, former NSA official and whistleblower
Thomas Drake told
DailyDot.com in July 2013 that FAIRVIEW was for tapping into the world's intercontinental fiber-optic cables and "to own the Internet". According to Drake it was an umbrella program with other programs, like BLARNEY, underneath it.
Similarly speculative was
Bill Binney, also a former NSA official who left and became a whistleblower in 2001. On multiple occasions he
said that a map showing the FAIRVIEW tapping points
proofs that NSA collects "content and metadata on US citizens" because those collection points are spread across the country:
 Slide from an NSA presentation as shown on the Brazilian
Slide from an NSA presentation as shown on the Brazilian
television show Fantástico on September 8, 2013
The new revelations by The New York Times and Pro Publica have now shown that the explanations by both Drake and Binney were misleading: FAIRVIEW is neither an overarching internet tapping program, nor is it collecting communications of US citizens.
Cover namesClosest to the truth came NSA historian
Matthew Aid, who in an article by
The Washington Post from October 2013, said that STORMBREW is the NSA alias used for Verizon, while FAIRVIEW stands for AT&T.
That's the right connection, although STORMBREW and FAIRVIEW aren't the cover names for these companies themselves, but the code words for the programs under which NSA cooperates with these telecoms.
The cover name for AT&T itself (at least under the BLARNEY program) is probably LITHIUM and for Verizon ARTIFICE. Cover names for other, but yet unidentified US telecoms are ROCKSALT, SERENADE, STEELKNIGHT and WOLFPOINT - their actual names are in the Exceptionally Controlled Information (ECI) compartment
WHIPGENIE (WPG).
Although Snowden seems to have had no access to that ECI compartment, reporters for
Pro Publica were able to identify both companies based upon various details found in the NSA documents about the STORMBREW and FAIRVIEW programs.
Legal authoritiesThe actual purpose of FAIRVIEW can be learned from an NSA
presentation, which clearly says the program is for collecting communications of foreign targets at collection points that are inside the United States. Two
other excerpts say that FAIRVIEW is also used for current and future "cyber plans", which probably include searching for malware signatures.
All this happens under three different legal authorities, and for each there's a different
http://firsttimetheviewbranding.blogspot.com /p/sigint.html">SIGINT Activity Designator (SIGAD):
Traditional FISA:
- Communications of persons being agents of foreign powers or connected to international terrorist groups
- Individualized warrant needed from the FISA Court
- Internet traffic only (SIGAD: US-984T)
Section 702 FAA:
- Communications of foreigners/with one end foreign
- Must be justified under an annual FAA Certification
- All kinds of internet traffic (SIGAD: US-984XR)
- Telephone traffic (SIGAD: US-984X2)
Transit Authority:
- Communications with both ends foreign
- No external approval required
- Internet traffic: only e-mail (SIGAD: US-990)
- Telephony: according to "Directory ONMR" (SIGAD: US-990)
For collection under Transit Authority, the presentation says that communications "must be confirmed foreign-to-foreign", which is ensured by filters at the actual tapping points (see stage 1 of the
dataflow, down below).
These filters only forward authorized traffic to the selection engines, which then pick out the communications that match with strong selectors, like e-mail addresses, phone numbers, etc. These selectors are entered into the system by analysts using the tasking tools
UTT, CADENCE (for internet) and OCTAVE (for telephony).
Examples of such selected, authorized traffic can be seen in a number of slides that were shown in a
Fantástico report from July 9, 2013. They are from a presentation that has not yet been released. These slides contain maps, which show the amount of internet traffic to countries like North Korea, Russia, USA and Iran, as seen on March 4-5, 2012.
Scroll here >
In the first slide we see for example internet traffic (DNI) to USA, which has been determined to be foreign-to-foreign and may therefore be collected under Transit Authority. As such, front-end filters forwarded this traffic to the selection engines for further filtering.
The slide below has a map showing the internet traffic to USA, which is eligible for collection under FAA authority:
The next slide shows a list of "Top 20 USAi domains (.pk)" which where tracked between February 15, 2012 and March 11, 2012:
A map representing "1 Day view of authorized (FAA ONLY) DNI traffic volumes to North Korea within FAIRVIEW environment", which means internet traffic which is authorized for collection under FAA authority:
Next is a list op "Top 20 North Korean domains (.kp)" which where tracked between February 15, 2012 and March 11, 2012. Note that only two websites generate notable traffic, all other have less than 1 Kbps:
A map showing internet traffic to Iran, which is eligible for collection under FAA authority:
A map showing internet traffic to Russia, which is authorized for collection under Transit authority:
Determining what traffic is foreign is done by filtering based upon telephone country codes and internet IP addresses. For telephony this is quite reliable, but particularly for internet traffic, the speaker's notes for another NSA
presentation admit that it is difficult to proof the foreigness. Therefore, it is occasionally discovered that one end of an intercept is actually in the US, which then has to be reported as a "domestic incident".
Tapping pointsOne of the most interesting new documents is an NSA
presentation from 2010 about the Corporate Partner Accesses, which has the map for the FAIRVIEW program with all the domestic dots, but this time with the explaining legend:
From the legend in combination with the dots on the map, we learn that under the FAIRVIEW program, NSA at that time had access points at the following parts of the AT&T network:
- Peering Link Router Complexes (8)
- VoIP Router Complexes (26, planned: 0)
- Hub VoIP Router Complex (1, planned: 30)
- Program Cable Stations (9, planned: 7)
- Non-Program Cable Stations (0)
- RIMROCK 4ESS Circuit Switches (16)
- Program Processing Site (1)
One important thing is that most of the markers inside the US do not represent traditional cable tapping points like those along the borders, but are current and planned accesses to
Voice over IP communications. Here's some explanation about the other types of access points too:
Peering Link Router Complex
NSA has 8 access points at AT&T Peering Link Router Complexes. According to Pro Publica they correspond to AT&T's Service Node Routing Complexes (SNRCs), where other communication providers connect to the AT&T backbone through OC-192 and 10GE fiber-optic cables. For NSA, this means they can catch traffic from those other providers too. This backbone access is codenamed SAGURA or SAGUARO. The 8 facilities are in:
- Seattle
- San Francisco
| | - Los Angeles
- Dallas
| | - Chicago
- Atlanta
| | - New York City
- Washington DC
|
It was this kind of access point that was/is in Room 641A in San Francisco, as was exposed by Mark Klein during a lawsuit in 2006. Klein told that the equipment in room 641a was installed early 2003, which could fit the turning on of "a new DNI (Digital Network Intelligence) collection capability" in September of that year.
VoIP Router Complex
The largest number of active access points, 26, are at VoIP Router complexes, which are apparently used for routing voice communications over IP networks, like the internet. No new accesses of this kind were plannend, but expansion seems to be in the next category:
Hub VoIP Router Complex
In the map from 2010 we see only one active access at a Hub VoIP Router Complex, which is somewhere near New York City (maybe in Florham Park, NJ, where AT&T has a data warehouse and its laboratory?). Access to VoIP communications was clearly seen as something that needed expansion, as 30 locations are marked as a planned access point. Unfortunately, no documents have yet been released about this effort.
 Map of the US internet backbone network of AT&T in 2009
Map of the US internet backbone network of AT&T in 2009
(Source: AT&T brochure - Click to enlarge)
Program Cable Station
At the time of the presentation, there were 9 AT&T cable stations with a tapping facility, and another 7 for which that was planned. For an article on Pro Publica, it was found out that 9 of these active and planned stations in the continental US correspond to cable landing stations owned by AT&T.
There are also two active and five planned accesses at cable landing points which are probably located in Hawaii and Puerto Rico. Some of the active facilities are in:
- Nedonna Beach, Oregon
- Point Arena, California
- San Luis Obispo, California
- Tuckerton, New Yersey
- West Palm Beach, Florida
RIMROCK 4ESS Circuit Switch
These facilities refer to a 4ESS switch, which is used for long-distance telephone switching. Approximately 100 of these switches are operated by AT&T, but according to the map, only 16 of them have a tapping facility codenamed TOPROCK. Except for two, they are situated along the US border, so seem to be for collecting (the metadata of) in- and outgoing phone calls. These sites appear to be in or near:
- Seattle
- Spokane
- Sacramento
- Los Angeles
| | - San Diego
- Albuquerque
- San Antonio
- Lansing
| | - Atlanta
- Pittsburgh
- Buffalo
| | - Kingston
- Hartford (2)
- New York City (2)
|
Program Processing Site
Finally, there's one centralized Program Processing Site, which is codenamed PINECONE. The map indicates that it's situated somewhere near the AT&T cable landing station of Tuckerton in New Jersey.
 The AT&T intercontinental cable landing station in Tuckerton, New Jersey,
The AT&T intercontinental cable landing station in Tuckerton, New Jersey,
which got a fake facade when residences were build around it.
(Photo: Bing maps - Click to enlarge)Seen for the first time is an NSA
presentation from 2012 with five diagrams showing the dataflow for the various collection methods under the FAIRVIEW program. There are diagrams for:
- Transit internet content (US-990)
- Transit internet metadata (US-990)
- Transit telephony metadata and SMS (US-990)
- FISA e-mail content (US-984T)
- FISA internet content (US-984T)
There are no diagrams for FAIRVIEW collection under the authority of section 702 FAA.
 Dataflow for internet content collected under the
Dataflow for internet content collected under the
FAIRVIEW program under Transit Authority
(Click to enlarge)These diagrams show that processing the data from tha various collection points takes places in 3 different stages at 3 different locations:
1. Access and processing at the partner company
2. Site processing in a central secure facility
3. Processing and storage at NSA headquarters
Here's a description of what roughly happens during these 3 stages:
1. Access and processing at the partner companyIn the first stage, AT&T provides access to internet and telephone cables and does some filtering and processing right at the various tapping points:
- For the internet collection, we see that the traffic is split at the switches where AT&T's own accesses, as well as peering partner's cables connect to the AT&T Common Back Bone (CBB).
This duplicated traffic goes to one or more routers, where "Foreign IP Filtering" takes place to select foreign and discard domestic traffic. The remaining data stream is then sent over to the central processing facility of the second stage, probably over OC-48 links of 2,4 Gbit/s. The same happens with traffic from other cable access points codenamed MESA.
It was this kind of installation that Mark Klein discovered in Room 641A in the SBC building in San Francisco in 2006. Many people assumed that in this way, NSA was able to store everything that runs over those cables, including American's communications, but now we know that filters ensure that only foreign traffic is sorted out for further processing.
Update:
Klein also testified that in room 641A there was equipment from Narus, which can be used to sessionize and filter data streams, but this is not seen in the diagrams. Maybe, after the exposure of room 641A, NSA moved that kind of equipment from the actual AT&T tapping points to the centralized processing facility codenamed PINECONE.
According to an NSA glossary, there are tens of thousands access links to the AT&T Common BackBone, which "would make 100% coverage prohibitively expensive". Therefore, NSA's Operations and Discovery Division (ODD) worked with AT&T to rank the access routers, and (only?) 8 router uplinks were deemed of high SIGINT interest and subsequently nominated for monitoring.
- Telephone metadata under Transit Authority are collected from Foreign Gateway Switches and "ATPs", by a "CNI [Calling Number Identification] & Call Processor" in facilities codenamed TOPROCK. These metadata are also sent over to the central processing facility of the second stage.
 One of the doors to room 641A in the building of AT&T in San Francisco,
One of the doors to room 641A in the building of AT&T in San Francisco,
where there's an access point to the AT&T Common BackBone
The second stage comprises processing which takes place at a central location, in a highly secured building, a
Sensitive Compartmented Information Facility (SCIF), which for the FAIRVIEW program is codenamed PINECONE. The equipment there is partly controlled by the partner company and partly by NSA.
Processing data from the many tapping points under the FAIRVIEW program at one central facility is only possible when already large amounts have discarded during the first stage. The remaining data stream is probably
sent (unencrypted) to PINECONE over dedicated links within the AT&T network.
- Internet data arrive at IP Routers (IPRs) and via IP Processors (IPPs) go to an "Information Media Manager Distribution Box". Internet metadata then go directly to MAILORDER. This device sends them to NSA headquarters (NSA-W), where they are received by another MAILORDER box.
Until now, MAILORDER was known as a tool for transferring data, but now it becomes clear that MAILORDER is also the device that encrypts the data so they can be transmitted safely from the PINECONE facility to NSA headquarters.
Before going to MAILORDER, internet content has to pass another box codenamed COURIERSKILL/CLEARSIGHT. This device also gets an input from the CADENCE tasking tool at NSA headquarters: the selectors for filtering.
Therefore, COURIERSKILL/CLEARSIGHT is the device that sorts out the communications that match the e-mail addresses and other identifiers as requested by NSA analysts. For e-mail collection under FISA authority, this filtering is done (directly) by XKEYSCORE.
After passing GATEKEEP, which could be some kind of access control system, the filtered internet content of interest goes to MAILORDER to be sent over to Fort Meade.
- Telephone metadata and SMS messages also pass an "Information Media Manager Distribution Box", which is connected to an unknown device marked NGTPD. Via MAILORDER, these data too are sent over to NSA headquarters.
3. Processing and storage at NSA headquartersIn the third and final stage, which is at NSA headquarters, the data from the central processing facility PINECONE arrive at a MAILORDER box, which is on the FAIRVIEW Local Area Network (LAN) codenamed HIGHDECIBEL.
From this LAN, the data are sent to NSA's core corporate network, again via secure MAILORDER transmission, to be stored in the various and meanwhile well-known databases, like PINWALE, MAINWAY, MARINA, FASCIA and DISHFIRE.
- Internet content first passes FISHWAY, which is a "Data Batching & Distribution System", and then SCISSORS. The latter was first seen in the earliest PRISM slides, and is a "Data Scanning, Formatting & Distribution System", as we learn from this diagram.
Raw internet content and e-mails collected under FISA authority are stored in the RAGTIME partition of the PINWALE database and are classified as TOP SECRET//SI-ECI RGT//REL [...].
- Internet metadata first pass FALLOUT, which is an internet metadata ingest processor/database, while telephone metadata and SMS go to FASCIA, which has the same function for this type of data.
 Overview of the numbers of data collected under the FAIRVIEW program
Overview of the numbers of data collected under the FAIRVIEW program
(Click to enlarge)According to one of the newly disclosed NSA
documents, the internet access under the FAIRVIEW program was initially used only for collecting e-mail messages. In 2003, this resulted in more than one million e-mails a day being forwarded to the keyword selection system at NSA headquarters.
This number had risen to 5 million a day in 2012, which remained after applying some kind of "3 Swing Algorithm" to 60 million foreign-to-foreign e-mail messages that were captured by FAIRVIEW every day under Transit Authority - according to the speaker's notes for an NSA
presentation from 2012.
Again we see a huge amount of data passing (which in de documents is called "captured" by) the FAIRVIEW tapping points, but that filters only select a small part which is then forwarded to the NSA for further selection. The 5 million e-mail messages a day in 2012 made 150 million a month and 1,8 billion a year.
BOUNDLESSINFORMANTThe most recent numbers of the data collected under FAIRVIEW can be derived from a chart from the NSA's
BOUNDLESSINFORMANT tool, which was published in May 2014 as part of Glenn Greenwald's book No Place to Hide:
During the one month period between December 10, 2012 and January 8, 2013, exactly 6.142.932.557 metadata records were counted for collection under Transit Authority, which for the FAIRVIEW program is denoted by the SIGAD US-990.
This means the numbers for FAIRVIEW collection under FISA and section 702 FAA authority are not included in this chart. But in those cases, only communications related to specific e-mail addresses or similar identifiers are collected, which results in far smaller numbers: according to a 2011
FISA Court ruling (pdf), Upstream collection under section 702 FAA resulted in just 22 million "internet communications" each year.
The over 6 billion records for FAIRVIEW account for only 3,75% of the
http://firsttimetheviewbranding.blogspot.com /2014/06/some-numbers-about-nsas-data-collection.html#ssocollection">total number of data the NSA collects through its cable tapping programs, which is remarkably small given the large number of access points at major internet cables and switches.
Tech detailsIn the lower part, the pie chart shows that under Transit Authority, roughly the following number of records were counted for FAIRVIEW:
- 87% or 5,3 billion:
Personal Communications Services (PCS, cell phone, etc)
- 2% or 122 million:
Mobile communications-over-IP (MOIP)
- 8% or 488 million:
Public Switched Telephone Network (PSTN)
- 3% or 183 million: Internet communications (DNI)
As reflected by the bar chart, the overwhelming majority of data come from foreign-to-foreign telephone communications, mostly from cell phones. Because there's no dataflow diagram for the content of phone calls, it's possible that this is only telephone
metadata and SMS messages.
Only about 3% comes from foreign-to-foreign e-mail messages, for which some 183 million metadata records were counted. This number comes close to the roughly 150 million e-mails a month that were processed in 2012, which could indicate that one metadata record equals one e-mail message.
The technology used to process 97% of these data is called FAIRVIEWCOTS, which could be a combination of the program's codename and the abbreviation COTS, which stands for Commercial-Of-The-Shelf equipment. Only nearly 3%, so probably the e-mail traffic, is processed by a hitherto unknown system codenamed KEELSON. Finally, a tiny number also went through SCISSORS.
Product reportsAfter the data have been collected and stored, analysts go through it, looking for useful intelligence information and put that in so-called product reports. A slide from a 2012
presentation about SSO's Corporate Portfolio, shows the Top Ten programs based upon the product reports that were prepaired during the fiscal year 2010-2011:
We see that with 7357 product reports, US-990, which is FAIRVIEW collection under Transit Authority, ranks as the second most productive source. However, 4 times more reports came from collection under section 702 FAA, which is not only derived from PRISM, but also from the STORMBREW and FAIRVIEW programs.
Although below the program ranking first, there are not very big differences in the numbers of reports, the chart still shows how focused FAIRVIEW collection must be: the 3,75% of the data it pulls in, is apparently so useful that it results in a big number of product reports.
From a different
presentation, we have a similar diagram with the numbers for the fiscal year 2009-2010:
CooperationThe
FAIRVIEW map also mentions a close partnership with the FBI. Under the PRISM program it's the FBI that actually picks up the data at the various internet companies, but for Upstream collection, like under FAIRVIEW, that's not the case: here the NSA has a
http://firsttimetheviewbranding.blogspot.com /2014/04/what-is-known-about-nsas-prism-program.html#slide13">direct relationship with the telecoms.
This leaves the option that the FBI (just
like the DEA and the CIA) is also a so-called customer of the program, meaning that the Bureau can request the collection of certain target's communications and access some of the data that NSA collected under FAIRVIEW.
Domestic metadataThe newly disclosed documents about FAIRVIEW also provide some new details about the bulk collection of domestic metadata, which is considered to be one of the most controversial activities of the NSA. Somewhat unexpected is that for AT&T this
happens under FAIRVIEW, instead of a separate program.
Internet metadataAn NSA
document from 2003 seems to be about bulk internet data. It says that FAIRVIEW also collected "metadata, or data about the network and the communications it carries" and that for September 2003 alone, "FAIRVIEW captured several trillion metadata records - of which more than 400 billion were selected for processing or storage".
This doesn't really sound like AT&T handed over bulk metadata indiscriminately, but it would fit how it's described in the 2009
STELLARWIND-report (in which, according to Pro Publica, AT&T is mentioned as "Company A") about the collection efforts under the
President's Surveillance Program (PSP):
"In order to be a candidate for PSP IP metadata collection, data links were first vetted to ensure that the preponderance of communications was from foreign sources, and that there was a high probability of collecting al Qaeda (and affiliate) communications. NSA took great care to ensure that metadata was produced against foreign, not domestic, communications"
It seems that at that time, AT&T did hand over massive amounts of internet metadata from its domestic infrastructure, but also made sure these were not about American communications.
Update:
The "internet dragnet", that is, the bulk collection of internet metadata of domestic communications under the authority of section 402 FISA (at NSA called PR/TT) was first approved by the FISA Court on July 14, 2004. That means, the 400 billion metadata collected under FAIRVIEW in 2003 were not yet part of the PR/TT bulk collection, and accordingly not domestic.
It is still remarkable that AT&T was able to forward 400 billion metadata records a month just from its foreign communications: in 2012, the http://firsttimetheviewbranding.blogspot.com /2014/06/some-numbers-about-nsas-data-collection.html#volumes">total number of internet metadata that NSA collected worldwide was "just" 312 billion a month.
The 2003 document says these metadata were flowing to
http://firsttimetheviewbranding.blogspot.com /2016/01/section-215-bulk-telephone-records-and.html">MAINWAY, which appears to be not only for telephone records, but "NSA's primary tool for conducting metadata analysis" in general.
* One of the dataflow diagrams also shows that internet metadata first flow into MAINWAY, and from there to MARINA, which is the repository for internet metadata:
 Dataflow for internet metadata collected under the
Dataflow for internet metadata collected under the
FAIRVIEW program under Transit Authority
(Click to enlarge)About bulk telephone metadata there's an NSA
document from 2011. It says that as of September 2011, FAIRVIEW began handing over "1.1 billion cellular records a day in addition to the 700M records delivered currently" under the Business Record (BR) FISA authorization, which refers to section 215 of the USA PATRIOT Act.
It was already known that the major US telecoms handed over their metadata records of landline telephone calls, but here we see that AT&T also started doing so for cell phone calls.
And for the very first time we also have some numbers now: the total of 1,8 billion a day provided by AT&T make 54 billion a month and about 650 billion phone records a year. For comparison, in 2012, NSA's regular foreign collection resulted in a
http://firsttimetheviewbranding.blogspot.com /2014/06/some-numbers-about-nsas-data-collection.html#volumes">total number of 135 billion telephone records a month and 1,6 trillion a year.
The mobile phone metadata provided by AT&T were fed into the MAINWAY database to be used for contact chaining in order to "detect previously unknown terrorist threats in the United States". Before these records were handed over to NSA, AT&T
stripped off the location data, to comply with the FISA Court orders, that don't allow those data to be collected.
Apparently Verizon Wireless and T-Mobile US don't strip off these location data, so their cell phone records cannot be handed over to NSA, which therefore only gets
less than 30% of the domestic telephone metadata.
ConclusionThe reports by Pro Publica and The New York Times stress AT&T's "extreme willingness to help" the NSA, which some people consider bad and scary. But maybe this very close cooperation helps to make data collection as targeted and focused as possible. Apart from the domestic metadata collection under BR-FISA, the relatively small numbers of data collected under the FAIRVIEW program, appear to contain a lot of valuable foreign intelligence information.
The fear was that under FAIRVIEW, large numbers of American's communications were sucked up by the NSA. However, the documents and diagrams show that there are filter systems that for collection under Transit Authority only let foreign-to-foreign communications through. Collection under section 702 FAA is already about foreign targets outside the US, while under FISA authority there's an individualized FISA Court order.
Interesting questions that remain are about the function of the rapidly growing number of VoIP collection points, as well as about the scope of the cyber security effort, and how in these fields, NSA tries to protect the rights of American citizens.
Links and sources- Statement before the House Committee on the Judiciary on the FISA Amendments Act (pdf) (2016)
- Bruce Schneier: NSA's Partnership with AT&T
- Matthew Green: The network is hostile
- EmptyWheel.net: What’s a Little (or a Lot) Cooperation Among Spies?
- EmptyWheel.net: AT&T Pulled Cell Location for Its “Mobility Cell Data”
- Wired.com: AT&T Whistle-Blower's Evidence
- Atlantic-cable.com: History of the Atlantic Cable & Undersea Communications